Social Engineering & Physical Penetration Security Testing
Why do I need to test my physical security?
You spend a lot of money on security. This will involve the physical security of your buildings and facilities. You may have high security fencing, deadbolt door locks, CCTV cameras, intrusion detection systems, alarms, security guards, patrol dogs, HID entry cards, encryption of data, ID badges, biometric entry systems to name but a few security options. Your current security maybe providing the best security for you, your family or your business assets. All of these can be very good at protecting what is important to you, but are you really protected? Often the weakest link is the human factor. The staff member who could be taken in by a confidence trickster to gain access to your facility. Maybe the offender will just trick the staff member to transfer your money to another account controlled by the offenders?
Have you ever tested your security systems and protocols to see if they really work?
We have the knowledge and experience of decades in policing, walking the streets at night checking if doors are closed and locked, attending real life crime scenes, knowing how real criminals operate and the (MO) modus operandi criminals use. We have direct experience of dealing with human intelligence sources and speaking with criminals and bad actors as to how and why they would attack your assets. How offenders negotiate in kidnaps and ransomware incidents.
We can test your physical security and human assets
We can help solve these problems -
- knowing is your security budget being well spent?
- Am I getting a good (ROI) Return On Investment?
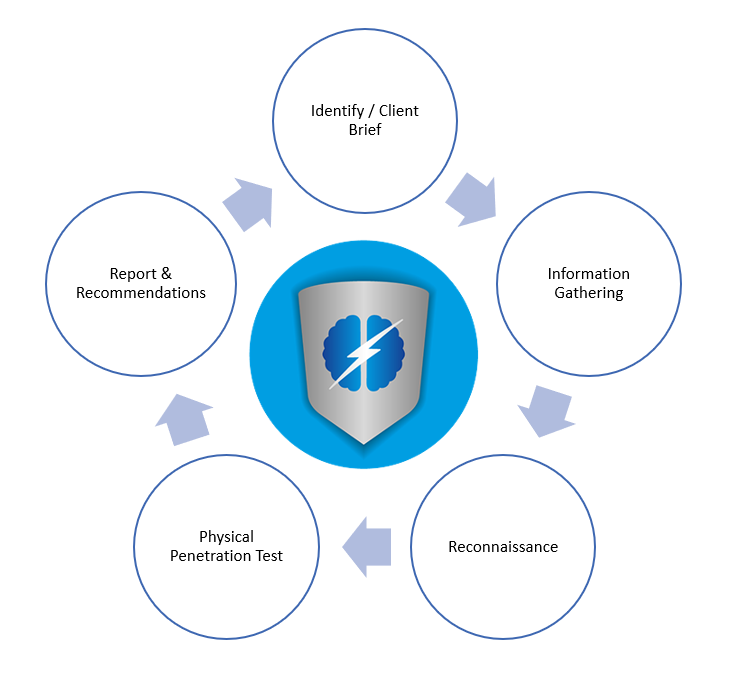
Our penetration testing workflow
- Identify / Client Brief
Make contact with us, and we will discuss what your security problems or issues are. We listen to what you want, and you stay in control. We will agree a scope of the testing and sign an agreement to ensure both parties know what will be tested. We also have NDA (Non Disclosure Agreements) that can be prepared to allow a free and open conversation to your security requirements. Not only that, but we will agree the scope of the assessment, what can and cannot be done, or taken (and returned) during the assessment.
- Information Gathering
We will use OSINT (Open Source Intelligence) from various sources to identify key online accounts or individuals. We will then pivot with this information to identify other accounts that maybe giving away more information than you realise. Armed with this information, we plan how a criminal or bad actor may use this information against you.
- Reconnaissance
We will use online mapping and physical reconnaissance of the target locations and facilities identified in the information gathering stage. We will identify the on-site security being deployed and formulate a plan to conduct the penetration test.
- Physical Penetration Test
Having a full intelligence picture on the target person or facility, we will conduct the physical penetration test within the time period agreed. Operatives used will have an appropriate pretext or cover story to help deal with any basic challenges they encounter. Operatives may take photos or video to prove access as agreed with the client.
- Report & Recommendations
We will produce a report including the problem profile, the intelligence gather phase, what the operatives have found during the physical assessment. We will provide recommendations as to what security is working and what is not. We will give recommendations as to how security could be improved. Likewise, we will also provide an executive summary overview of the assessment to help convey the key points that are raised.